Network Detection and Response
Next Generation Security And Data Management Solutions
Network Detection and response
(NDR) is a cybersecurity solution that continuously monitors an organization’s network to detect cyber threats & anomalous behaviour using non-signature-based tools or techniques and responds to these threats via native capabilities or by integrating with other cybersecurity tools/solutions.
How does Network Detection and Response work?
Network Detection and response (NDR) is a cybersecurity solution that continuously monitors an organizations network by collecting all network traffic for unprecedented visibility and using behavioural analytics, machine learning & artificial intelligence to detect cyber threats & anomalous behaviour and respond to these threats via native capabilities or by integrating with other cybersecurity tools/solutions.
Highly performant NDR solutions use advanced machine learning and artificial intelligence tools to model adversary tactics, techniques and procedures that are mapped in the MITRE ATT&CK framework to detect attacker behaviours with high precision. They surface security-relevant context, extract high-fidelity data, correlate events across time, users, and applications to drastically reduce time and effort spent in investigations. They also stream security detections and threat correlations to security information event management (SIEM) solutions for comprehensive security assessments.
NDR solutions move beyond merely detecting threats, responding to threats in real-time by native controls or by supporting a wide-range of integrations with other cybersecurity tools or solutions like security orchestration, automation, and response (SOAR).
Why does my organization need Network Detection and Response?
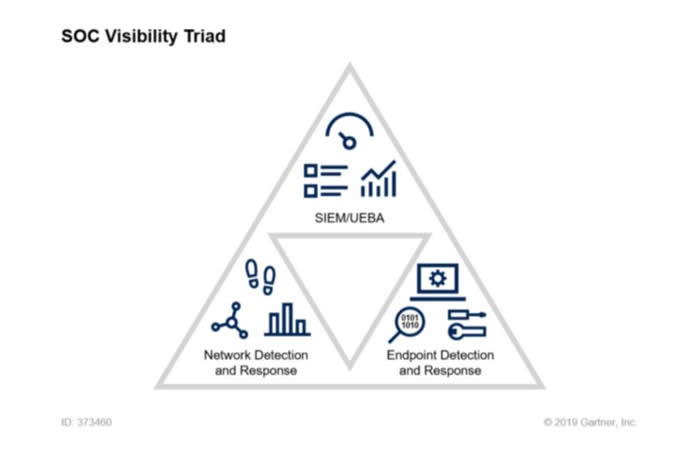
Gartner SOC visibility triad
NDR plays a pivotal role in securing your digital infrastructure.
Threat history is generally available in three places: network, endpoint and logs.
- Endpoint Detection and Response (EDR) provides a detailed ground-level view of the processes running on a host and interactions between them.
- Network Detection and Response (NDR) provides an aerial view of the interactions between all devices on the network.
- Security teams then configure Security Information and Event Management (SIEM) system to collect event log information from other systems and correlate between data sources.
Security teams that deploy these tools are empowered to answer a broad range of questions when responding to an incident or hunting for threats.
For example, they can answer: What did this asset or account do before the alert? What did it do after the alert? Can we find out when things started to turn bad?
NDR is most critical because it provides perspective where the others cannot.
For example, exploits that operate at the BIOS level of a device can subvert EDR or malicious activity may simply not be reflected in logs. But their activity will be visible by network tools as soon as they interact with any other system through the network.
Or advanced and sophisticated attackers use hidden encrypted HTTPS tunnels, that blend in with regular traffic, to launch a command and control (C2) session and use the same session to exfiltrate sensitive business and customer data and evade perimeter security controls but NDR solutions are extremely adept at detecting these behaviours.
Effective AI-driven network detection and response platforms collect and store the right metadata and enrich it with AI-derived security insights.
Effective use of AI can then drive the detection of attackers in real-time and perform conclusive incident investigations.
What are the benefits of Network Detection and Response?
Continuous visibility accross the network
Network Detection and Response cybersecurity solutions provide continuous visibility across all users, devices and technologies connected to the network, from data center to the cloud, from campus users to work from home users, from IaaS to SaaS, and from printers to IoT devices.
Behavioral analytics and AI for advanced threats detection
Leading NDR solutions use behavioral analytics and ML/AI to directly model attacker behaviors and detect advanced and persistent attacks with surgical precision. They avoid the deluge of low-fidelity and uninteresting alerts since they don’t detect anomalies, but rather, detect active attacks. They provide detection coverage for several phases of an attack lifecycle, including persistence, privilege escalation, defense evasion, credential access, discovery, lateral movement, data collection, C2 and exfiltration.
Improvement of security operations center (SOC) operational efficiency
Leading AI-driven NDR solutions are automatic and dramatically improve security detections and security operations center (SOC) operational efficiency despite organizations and teams being plagued by a chronic shortage of cybersecurity expertise & personnel by offering full attack reconstructions in natural language that provide analysts, all the information they need to act on alerts quickly and completely.
Ability to automatically respond and shut down attacks in real-time
In addition to detecting sophisticated attacks that operate discreetly and employ evasive techniques, NDR solutions offer the ability to automatically respond to serious attack via native controls and shut down an attack in real-time. Additionally they integrate with several cybersecurity products like EDR or cybersecurity solutions like SOAR.

Can we help you?
To find out more about how our Managed Services, or Solutions and how they can help your organisation to reduce cost and complexity while strengthening your security and business continuity position, please get in touch today.
